-40%
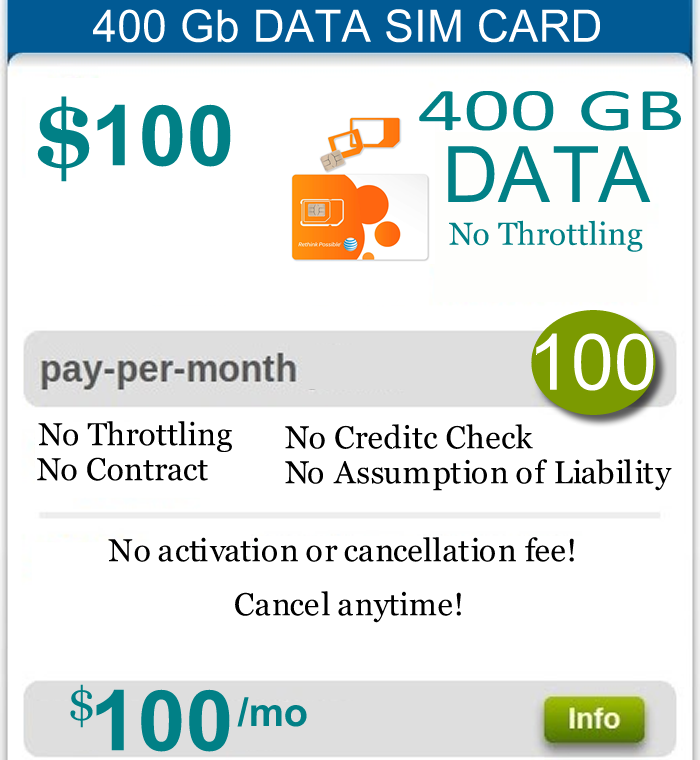
ATT 4G LTE Data Hotspot Plan NO CAPS 400 GB 0/Monthly/ REMOTE ACTIVATION
$ 52.8
- Description
- Size Guide
Description
PLEASE FOLLOW THE DIRECTIONS!REMOTE ACTIVATION ONLY
YOU WILL NEED A NEW SIM CARD
If you CAN NOT follow simple directions, we WILL NOT PROCESS YOUR REQUEST!
This is not a all you can eat plan. The fact that people are saying it’s truly unlimited on other listing is not true.
How ever this plan is the best much for your money.
You can really use up to 400 GB data without any problems.
Contact us if you already have a sim card so that we can activate it. New sim card !!!
When purchasing this item you agree to all terms and conditions that are listed in this listing
so please make sure to read all of our terms and conditions along with our Acceptable Use Policy in this listing.
Those who purchase this item will be shipped a New Sim Card!
0/month AT&T 4G LTE Unlimited Data Sim Card for Hotspots, Wireless Routers
This is not a "Data Connect" or "Grandfathered Plan" that gets shut down daily
Truly unlimited data. No Throttle. No Caps.
Are you one of the thousands of consumers that have been shut down by using a Data Connect or fictional Grandfathered Plan?
The reason for this is because AT&T shut down the illegal plans people were using.
What's special about this plan?
You will get truly unlimited data with no throttling on AT&T network
There's no throttling
No Cap
You can use this Rental Unlimited Data on any AT&T routers, hot-spots or routers. Please ask me if you are not sure what device is compatible with this plan.
Auto-pay signup. (2 days before your initial month is set to expire, you will receive a PayPal invoice that will allow you to pay your next months bill and sign up for auto-pay.
You can cancel anytime - there is no commitment whatsoever
Monthly Renewal:
1. Once your sim card is activated you will be charged 0 Per Month for the service.
2. Data Refill Cycle is Every 30 Days.
What's Included In Purchase
REMOTE ACTIVATION ONLY
Free Technical Support Anytime
EXPEDITED shipping available.
Payment Policy
Once your Sim Card is activated, you will be charged monthly from the activation date of your sim card.
After Purchase of Listing
Since our service is prepaid, we DO NOT offer returns / refunds / exchanges / or cancels on this item along with any and all fees / taxes / shipping costs associated with this item.
2 days before your initial months plan is to expire, you will receive a PayPal invoice that will allow you to pay the next months bill and set you up for auto-pay.
ACCEPTABLE USE POLICY
THE FOLLOWING TERMS APPLY TO YOUR (WHICH INCLUDES ANYONE WHO USES OUR SERVICES) USE OF AND ACCESS TO ANY CG ELECTRONICS , TOGETHER WITH OUR AGENTS, (COLLECTIVELY "CG CELLULAR" OR "CG ELECTRONICS" ), OWNED OR OPERATED WEBSITE ("WEBSITE") AS WELL AS ANY ELECTRONIC TRANSMISSION SENT, RECEIVED, POSTED, ACCESSED, OR STORED VIA ANY NETWORK ("NETWORK").
COVERAGE OF THIS POLICY AND AGREEMENT
IN ADDITION TO OTHER AGREEMENTS BETWEEN YOU AND CG ELECTRONICS, THESE TERMS EXPLAIN THE POLICIES THAT GOVERN YOUR ACCESS TO AND USE OF OUR WEBSITE AND NETWORK. BY ACCESSING OR USING OUR WEBSITE OR NETWORK, YOU AGREE TO THESE TERMS (COLLECTIVELY THE "POLICY"), AS CG ELECTRONICS MAY MODIFY IT FROM TIME TO TIME. MODIFICATIONS TO THIS POLICY ARE EFFECTIVE UPON ITS POSTING ON OUR WEBSITE. IF YOU DO NOT AGREE TO ACCEPT AND COMPLY WITH THE POLICY, THEN DO NOT ACCESS OR USE OUR WEBSITE OR NETWORK.
ILLEGAL OR HARMFUL USE
YOU MAY ACCESS AND USE OUR WEBSITE AND NETWORK ONLY FOR LAWFUL PURPOSES. YOU ARE RESPONSIBLE FOR ANY TRANSMISSION YOU SEND, RECEIVE, POST, ACCESS, OR STORE VIA OUR NETWORK, INCLUDING THE CONTENT OF ANY COMMUNICATION. TRANSMITTING, DISTRIBUTING, OR STORING ANY MATERIAL THAT VIOLATES ANY APPLICABLE LAW IS PROHIBITED. ADDITIONALLY, THE FOLLOWING NON-EXHAUSTIVE LIST DETAILS THE KINDS OF ILLEGAL OR HARMFUL CONDUCT THAT IS PROHIBITED:
INFRINGEMENT: INFRINGEMENT OF INTELLECTUAL PROPERTY RIGHTS OR OTHER PROPRIETARY RIGHTS INCLUDING, WITHOUT LIMITATION, MATERIAL PROTECTED BY COPYRIGHT, TRADEMARK, PATENT, TRADE SECRET, OR OTHER INTELLECTUAL PROPERTY RIGHT. INFRINGEMENT MAY RESULT FROM THE UNAUTHORIZED COPYING, DISTRIBUTION, AND/OR POSTING OF PICTURES, LOGOS, SOFTWARE, ARTICLES, MUSICAL WORKS, AND VIDEOS.
OFFENSIVE MATERIALS: DISSEMINATING OR POSTING MATERIAL THAT IS UNLAWFUL, LIBELOUS, DEFAMATORY, OBSCENE, INDECENT, LEWD, HARASSING, THREATENING, HARMFUL, INVASIVE OF PRIVACY OR PUBLICITY RIGHTS, ABUSIVE, INFLAMMATORY, OR OTHERWISE OBJECTIONABLE. WITHOUT LIMITING THE FOREGOING, YOU MAY NOT ACCESS OR USE OUR WEBSITE OR NETWORK IN ANY MANNER FOR THE TRANSMISSION OR DISSEMINATION OF IMAGES CONTAINING CHILD PORNOGRAPHY.
EXCESSIVE UTILIZATION OF NETWORK RESOURCES: CONSUMING A DISPROPORTIONATE AMOUNT OF AVAILABLE NETWORK RESOURCES RESULTING IN THE POTENTIAL TO DISRUPT OR DEGRADE THE NETWORK OR NETWORK USAGE BY OTHERS. THE DETERMINATION OF WHAT CONSTITUTES EXCESSIVE USE DEPENDS ON THE SPECIFIC STATE OF THE NETWORK AT ANY GIVEN TIME. EXCESSIVE USE IS DETERMINED BY RESOURCE CONSUMPTION RELATIVE TO THAT OF A TYPICAL INDIVIDUAL USER OF THE NETWORK AND NOT BY THE USE OF ANY PARTICULAR APPLICATION.
EXPORT VIOLATIONS: VIOLATIONS OF EXPORT LAWS, REGULATIONS, AND RULES, INCLUDING, WITHOUT LIMITATION, VIOLATIONS OF THE EXPORT ADMINISTRATION ACT AND THE EXPORT ADMINISTRATION REGULATIONS ADMINISTERED BY THE DEPARTMENT OF COMMERCE.
FRAUDULENT CONDUCT: (1) CONDUCTING FRAUDULENT BUSINESS OPERATIONS AND PRACTICES; (2) OFFERING OR DISSEMINATING FRAUDULENT GOODS, SERVICES, SCHEMES, OR PROMOTIONS (E.G., MAKE-MONEY-FAST SCHEMES, CHAIN LETTERS, AND PYRAMID SCHEMES); AND (3) INDIVIDUAL OR BUSINESS REPRESENTATION AS AN AUTHORIZED 3RD PARTY AFFILIATION OR AGENT FOR A BUSINESS ENTITY (E.G., CG ELECTRONICS ) WITHOUT THE BUSINESS' PRIOR CONSENT.
FALSIFICATION/IMPERSONATION: USING THE NETWORK TO IMPERSONATE ANY PERSON OR ENTITY; FALSELY STATE OR OTHERWISE MISREPRESENT YOUR AFFILIATION WITH ANY PERSON OR ENTITY; OR CREATE A FALSE IDENTITY FOR THE PURPOSE OF MISLEADING OTHERS. WITHOUT LIMITING THE FOREGOING, YOU MAY NOT USE INVALID OR FORGED HEADERS, INVALID OR NON-EXISTENT DOMAIN NAMES, OR OTHER MEANS OF DECEPTIVE ADDRESSING.
FAILURE TO ABIDE BY THIRD-PARTY NETWORK OR WEBSITE POLICIES: VIOLATING THE RULES, REGULATIONS, OR POLICIES THAT APPLY TO ANY THIRD-PARTY NETWORK, SERVER, COMPUTER DATABASE, OR WEBSITE THAT YOU ACCESS.
HARMFUL CONTENT: DISSEMINATING OR POSTING CONTENT THAT IS HARMFUL TO THE NETWORK OR OTHER USERS OF THE NETWORK INCLUDING, WITHOUT LIMITATION, VIRUSES, TROJAN HORSES, WORMS, TIME BOMBS, ZOMBIES, CANCEL-BOTS, OR ANY OTHER COMPUTER PROGRAMMING ROUTINES THAT MAY DAMAGE, INTERFERE WITH, SECRETLY INTERCEPT OR SEIZE ANY SYSTEM, PROGRAM, DATA, OR PERSONAL INFORMATION.
ELECTRONIC COMMUNICATIONS
YOU MAY NOT DISTRIBUTE, PUBLISH, OR SEND THROUGH OUR NETWORK: (1) ANY SPAM, INCLUDING ANY UNSOLICITED ADVERTISEMENTS, SOLICITATIONS, COMMERCIAL E-MAIL MESSAGES, INFORMATIONAL ANNOUNCEMENTS, OR PROMOTIONAL MESSAGES OF ANY KIND; (2) CHAIN MAIL; (3) NUMEROUS COPIES OF THE SAME OR SUBSTANTIALLY SIMILAR MESSAGES; (4) EMPTY MESSAGES; (5) MESSAGES THAT CONTAIN NO SUBSTANTIVE CONTENT; (6) VERY LARGE MESSAGES OR FILES THAT DISRUPT A SERVER, ACCOUNT, NEWSGROUP, OR CHAT SERVICE; OR (7) ANY MESSAGE THAT IS CATEGORIZED AS “PHISHING.”
LIKEWISE, YOU MAY NOT: (1) PARTICIPATE IN SPIDERING, HARVESTING, OR ANY OTHER UNAUTHORIZED COLLECTION OF E-MAIL ADDRESSES, SCREEN NAMES, OR OTHER IDENTIFIERS OF OTHERS OR PARTICIPATE IN USING SOFTWARE (INCLUDING "SPYWARE") DESIGNED TO FACILITATE SUCH ACTIVITY; (2) COLLECT RESPONSES FROM UNSOLICITED MESSAGES; OR (3) USE ANY OF OUR MAIL SERVERS OR ANOTHER SITE'S MAIL SERVER TO RELAY MAIL WITHOUT THE EXPRESS PERMISSION OF THE ACCOUNT HOLDER OR THE SITE.
NETWORK SECURITY AND INTEGRITY
YOU MAY NOT VIOLATE THE SECURITY OF OUR NETWORK IN ANY WAY. SUCH VIOLATIONS MAY RESULT IN CRIMINAL OR CIVIL LIABILITY. CG ELECTRONICS MAY, BUT IS NOT OBLIGATED TO, INVESTIGATE ANY VIOLATION OF OUR NETWORK. CG ELECTRONICS MAY COOPERATE WITH LAW ENFORCEMENT WHERE CRIMINAL OR UNAUTHORIZED ACTIVITY IS SUSPECTED. BY USING CG ELECTRONICS PRODUCTS AND SERVICES OR SENDING, RECEIVING, POSTING, ACCESSING, OR STORING ANY ELECTRONIC TRANSMISSION VIA OUR NETWORK, YOU AGREE TO COOPERATE IN ANY SUCH INVESTIGATION. EXAMPLES OF NETWORK SECURITY VIOLATIONS INCLUDE, WITHOUT LIMITATION:
HACKING: UNAUTHORIZED ACCESS TO OR USE OF DATA, SYSTEMS, OR NETWORKS, INCLUDING ANY ATTEMPT TO PROBE, SCAN OR TEST THE VULNERABILITY OF A SYSTEM OR NETWORK OR TO BREACH SECURITY OR AUTHENTICATION MEASURES WITHOUT THE EXPRESS PRIOR AUTHORIZATION OF THE OWNER OF THE SYSTEM OR NETWORK.
INTERCEPTION: UNAUTHORIZED MONITORING OF DATA OR TRAFFIC ON ANY NETWORK OR SYSTEM WITHOUT THE EXPRESS PRIOR AUTHORIZATION OF THE OWNER OF THE SYSTEM OR NETWORK.
INTENTIONAL INTERFERENCE: INTERFERENCE WITH SERVICE TO ANY USER, HOST, OR NETWORK INCLUDING, WITHOUT LIMITATION, DENIAL-OF-SERVICE ATTACKS, MAIL BOMBING, NEWS BOMBING, OTHER FLOODING TECHNIQUES, DELIBERATE ATTEMPTS TO OVERLOAD A SYSTEM, AND BROADCAST ATTACKS.
FALSIFICATION OF ORIGIN OR ROUTING INFORMATION: USING, SELLING, OR DISTRIBUTING IN CONJUNCTION WITH THE NETWORK, ANY COMPUTER PROGRAM DESIGNED TO CONCEAL THE SOURCE OR ROUTING INFORMATION OF ELECTRONIC MAIL MESSAGES IN A MANNER THAT FALSIFIES AN INTERNET DOMAIN, HEADER INFORMATION, DATE OR TIME STAMP, ORIGINATING E-MAIL ADDRESS, OR OTHER IDENTIFIER.
AVOIDING SYSTEM RESTRICTIONS: USING MANUAL OR ELECTRONIC MEANS TO AVOID ANY LIMITATIONS ESTABLISHED BY CG ELECTRONICS OR ATTEMPTING TO GAIN UNAUTHORIZED ACCESS TO, ALTER, OR DESTROY ANY INFORMATION THAT RELATES TO ANY CG ELECTRONICS CUSTOMER OR OTHER END-USER. CG ELECTRONICS MAY, BUT IS NOT OBLIGATED TO, TAKE ANY ACTION IT DEEMS NECESSARY TO (1) PROTECT ITS NETWORK, ITS RIGHTS, OR THE RIGHTS OF ITS CUSTOMERS OR THIRD PARTIES, OR (2) OPTIMIZE OR IMPROVE ITS NETWORK, SERVICES, SYSTEMS, AND EQUIPMENT. YOU ACKNOWLEDGE THAT SUCH ACTION MAY INCLUDE, WITHOUT LIMITATION, EMPLOYING METHODS, TECHNOLOGIES, OR PROCEDURES TO FILTER OR BLOCK MESSAGES SENT THROUGH THE NETWORK. CG ELECTRONICS MAY, IN ITS SOLE DISCRETION AND AT ANY TIME, FILTER "SPAM" OR PREVENT "HACKING," "VIRUSES," OR OTHER POTENTIAL HARMS WITHOUT REGARD TO ANY PREFERENCE YOU MAY HAVE COMMUNICATED TO US.
INVESTIGATION AND ENFORCEMENT OF THIS POLICY
WE HAVE THE RIGHT, BUT ARE NOT OBLIGATED, TO STRICTLY ENFORCE THIS POLICY THROUGH SELF-HELP, ACTIVE INVESTIGATION, LITIGATION, AND PROSECUTION.
CG ELECTRONICS RESERVES THE RIGHT TO ACT IMMEDIATELY AND WITHOUT NOTICE TO RESTRICT, SUSPEND, OR TERMINATE YOUR USE OF THE NETWORK IF IT REASONABLY DETERMINES THAT YOUR CONDUCT MAY: (1) EXPOSE CG ELECTRONICS TO SANCTIONS, PROSECUTION, CIVIL ACTION, OR OTHER LIABILITY; (2) CAUSE HARM TO OR INTERFERE WITH THE INTEGRITY OR NORMAL OPERATIONS OF CG ELECTRONICS' NETWORK OR NETWORKS WITH WHICH CG ELECTRONICS IS INTERCONNECTED; (3) INTERFERE WITH ANOTHER CG ELECTRONICS CUSTOMER'S USE OF THE NETWORK; (4) VIOLATE ANY APPLICABLE LAW, RULE, OR REGULATION; OR (5) OTHERWISE PRESENT AN IMMINENT RISK OF HARM TO CG ELECTRONICS OR ITS CUSTOMERS.
CG ELECTRONICS HAS THE RIGHT, BUT NOT THE OBLIGATION, TO MONITOR OR RESTRICT ANY USES OF THE NETWORK THAT CG ELECTRONICS REASONABLY BELIEVES IN ITS SOLE DISCRETION VIOLATE THIS AUP. YOU ARE SOLELY RESPONSIBLE FOR ALL CONTENT THAT YOU TRANSMIT OR RECEIVE UTILIZING THE NETWORK, AND YOU ARE RESPONSIBLE FOR ABUSE OF YOUR ACCOUNT BY OTHERS.
WE MAY ALSO ACCESS AND DISCLOSE ANY INFORMATION (INCLUDING TRANSACTIONAL INFORMATION) RELATED TO YOUR ACCESS AND USE OF OUR NETWORK FOR ANY LAWFUL REASON, INCLUDING BUT NOT LIMITED TO: (1) RESPONDING TO EMERGENCIES; (2) COMPLYING WITH THE LAW (E.G., A LAWFUL SUBPOENA); (3) PROTECTING OUR RIGHTS OR PROPERTY AND THOSE OF OUR CUSTOMERS; OR (4) PROTECTING USERS OF THOSE SERVICES AND OTHER CARRIERS FROM FRAUDULENT, ABUSIVE, OR UNLAWFUL USE OF OR SUBSCRIPTION TO SUCH SERVICES. INDIRECT OR ATTEMPTED BREACHES OF THIS POLICY AND ACTUAL OR ATTEMPTED BREACHES BY A THIRD PARTY ON BEHALF OF A COMPANY, CUSTOMER, OR USER MAY BE CONSIDERED BREACHES OF THIS POLICYBY SUCH COMPANY, CUSTOMER, OR USER.
MISCELLANEOUS